The featured image was created with Limewire’s AI Studio.
Damn, I Got This Close To Fall Victim To A Phishing Attack!
Last week, I came dangerously close to falling for a well-designed financial phishing attack.
I was approached by someone claiming to be a general partner at a venture capital fund, offering me an advisor role to help the team analyze investment opportunities.
In this post, I will:
- Describe the phishing attempt
- Detail what happened step by step
- Explain how I almost fell for it
- Share what ultimately prevented me from being scammed
- Highlight the lessons I learned
Let’s jump in.
How The Phishing Attack Started
The attack began when I was contacted on Twitter by someone we’ll call Mr. X (his profile has since been reported and suspended). Mr. X claimed to be with a venture capital fund called 0xVentures, describing it as a “diverse group of founders, users, and researchers that invests in sector-disrupting projects.”
I checked out their website, which looked legitimate.
We engaged in casual and random conversations over several days, discussing various investment themes and opportunities.
At no point did I feel “pressured” or “misled.” It felt like a normal conversation with a like-minded person.

Key Moment #1 – The Offer
After a week of conversations, Mr. X asked if I was open to discussing an advisor role.
He mentioned that I had the experience and credentials they were looking for and that the position would come with adequate compensation, requiring about 3-4 hours of work per week.
Having started and sold my firm and invested in four startups, it’s not unusual for me to be offered roles or asked for advice.
I agreed to discuss it further and expressed my willingness to hear more about the opportunity.
Key Moment #2 – The Appointment
Mr. X then shared a link with me to help me choose a date and time for our upcoming call.
The scheduling page looked clean & professional, like this:
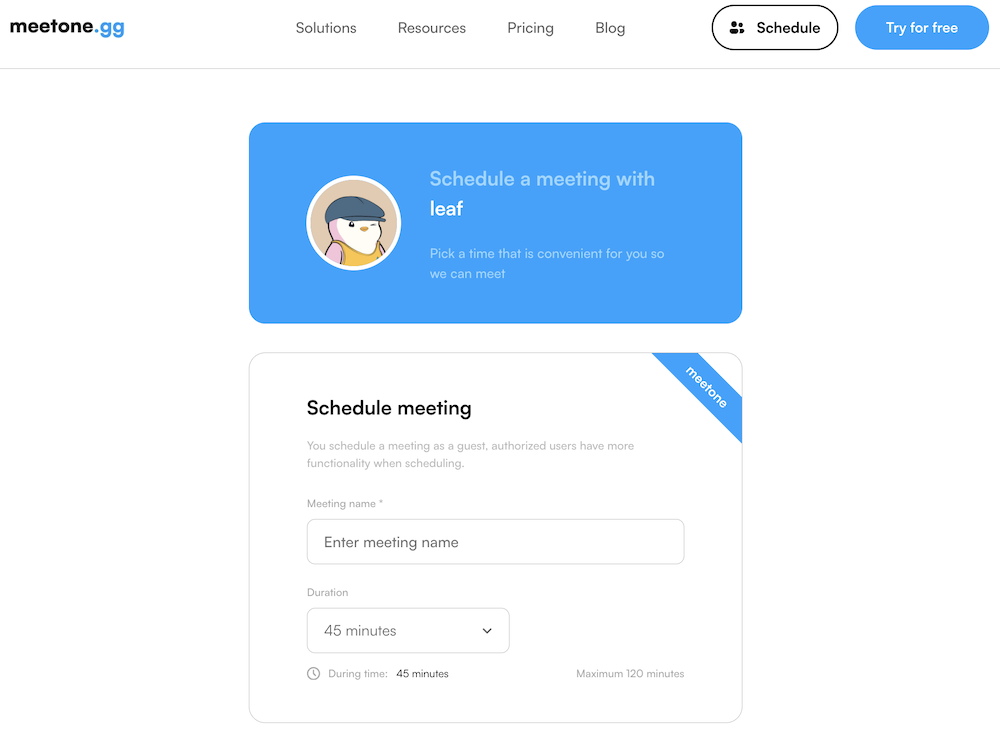
He mentioned that his entire back office uses a new calendar and video conferencing software, which is a portfolio company of 0xVentures, and described it as “super easy to use“.
Since I enjoy trying out new tech, I agreed and chose a date and time. The experience was smooth, and everything worked well.
I even checked reviews on Trustpilot and saw that the software had 10 positive ratings.
Key Moment #3 – The Installation
Now we come to the crucial part where it gets interesting.
I downloaded the conferencing app from the site and installed it.
Once the installation was complete, a window popped up, asking me in broken English to enter my password – see below.
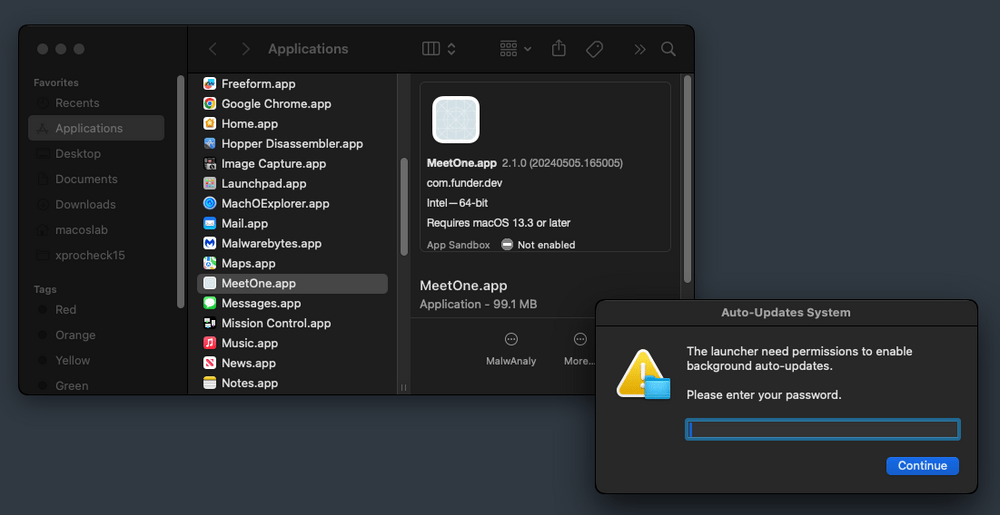
This is when I became extremely suspicious and decided not to take any action.
I couldn’t close the window, and it was floating above everything else, which was quite annoying. I’m sure many people would simply enter their password to get rid of it!
Instead, I decided to restart my computer and run my malware and virus protection app, Malwarebytes.
The Realization & How I Got Help
I ran Malwarebytes and instantly got the following warning message:
🚨🚨🚨 Threat secured – Meetone.gg is infected with malware: MacOS:Stealer-AB [Trj]. 🚨🚨🚨
Now I had the black-on-white proof.
I further shared the story in the Malwarebytes forum, and one of their tech specialists explained:
“What you downloaded is a Stealer malware disguised as an app called Meetone.App. It tries to steal your data if you enter your system password. Since you didn’t enter the password and restarted, you should be safe after deleting the Meetone App.”
If I had put in my password, this Trojan Horse Malware Stealer would disguise itself as a legitimate program but secretly steal sensitive information from my device.
The phishing attack scammer would have gained access to and stolen all my sensitive data such as
- all sorts of login credentials,
- credit card numbers,
- capture screenshots,
- even take control of my device,
- allowing the attacker to manipulate any data.
This could have resulted in disastrous financial & safety consequences.
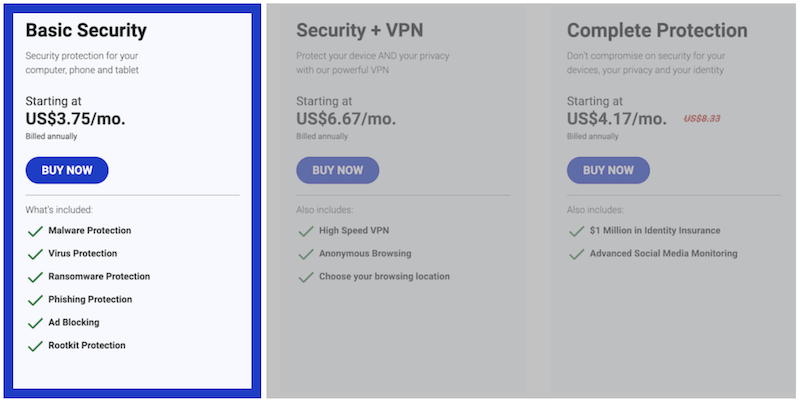
I can’t thank and recommend Malwarebytes enough for protecting me from this nasty phishing attack!
Sign up and get protection with their basic Malwarebytes package – at $3.75/mo it’s fantastic value.
Practical Tips & Key Takeaways
I was lucky to not have fallen victim to this social engineering phishing attack, but it also showed me how quickly it can happen. Here are my key takeaways:
- Get Malwarebytes – Pay for their basic version, and feel good being protected. Do it today!
- Own your infrastructure – Insist on using your infrastructure, e.g. your Google Meet/Zoom/Teams.
- Be careful – Don’t click on links provided in emails or messages of people you don’t know.
- Use a password manager – Use a password manager like LastPass to use different passwords for each site.
- Use multi-factor authentication – Protect your accounts by using 2Fa whenever possible.
- Do regular backups – Back up the data on your computer and phone to the cloud.
📘 Read Also
- The AI Investment Pyramid – Building A Balanced Portfolio
- My Exit Plan – When Is The Best Time To Sell?
- How To Spot A Financial Scam – 4 Important Tips
FAQ
How does a phishing attack work?
A phishing attack works by tricking you into providing sensitive information through deceptive emails, messages, or websites that appear legitimate. They often are good in socially-engineering a plot that is truly believable and convincing.
How to avoid a phishing attack?
Avoid phishing attacks by verifying the sender’s identity, not clicking on suspicious links, using security software, and regularly updating passwords. Stay vigilant and don’t trust strangers. Double-confirm and verify the identity of whoever you engage with online.
What is a phishing attack with an example?
Simply put, a phishing attack is a fraudulent attempt to steal sensitive or financial information from you. For example, receiving an email pretending to be from your bank asking you to verify your account details. Or a phishing attack scammer might try to send you a link to download a file, which actually is a trojan horse, lurking and sleeping on your computer, constantly sending the hacker information and files without you even noticing it.
How does a phishing attack happen?
Phishing attacks happen when you are deceived into providing personal information through fake communications that appear to be from trusted sources. The scammers are often very convincing and good in socially engineering a believable plot.





 Age when reaching FI: 40 in 2018
Age when reaching FI: 40 in 2018 Left the rat race: May 2017
Left the rat race: May 2017 Living in: Singapore
Living in: Singapore Number of kids: 2
Number of kids: 2





 Services I Love
Services I Love